Comprehensive Web Application Testing for Unbeatable Cybersecurity
In today’s fast-paced digital landscape, web applications play a crucial role in the success of businesses across various industries. However, cybercriminals exploit vulnerabilities in these web apps. To safeguard your online assets and protect against hackers, invest in expert web application testing. At Praetorian Secure, we take pride in offering high-end penetration testing services that fortify your web applications and APIs. Let us guide you to secure your digital assets and stay one step ahead of cyber threats.
Benefits Of Web App Penetration Testing
1. Stay Ahead Of Cybercriminals
2. Tailored Testing For Unique Needs
3. Discover Security Flaws
4. Remediation And Protection
Understanding Web Application Penetration Testing
Web application penetration testing goes beyond routine security assessments. It emulates the actions of a skilled hacker, critically analyzing your web application’s security vulnerabilities, weaknesses, and technical misconfigurations—just as a real attacker would target them. By simulating these attacks, we uncover potential risks and weaknesses, allowing you to take immediate action in eliminating vulnerabilities while maintaining seamless business operations.
Web App Security Testing Services
Our web app security testing services help you identify vulnerabilities in your web applications and mitigate risks. These web app security testing services include:
- Web Application Pen Testing –
Our web application penetration testing service involves simulating real-world attacks to identify vulnerabilities in your web applications. Our team of experts uses a combination of manual and automated testing techniques to identify potential security risks. - Web Application Security Assessment –
Our web application security assessment service involves a comprehensive review of your web applications to identify potential security risks. We use a combination of manual and automated testing techniques to identify vulnerabilities and provide recommendations for remediation. - Secure Code Review –
Our secure code review service involves a comprehensive review of your web application’s source code to identify potential security risks. We use a combination of manual and automated testing techniques to identify vulnerabilities and provide recommendations for remediation.
Varieties of Web App Penetration Testing
Authenticated Testing
Authenticated web app testing simulates an attacker who has breached your external security or has obtained valid user credentials through phishing. This comprehensive testing reveals the true extent of potential damage a successful cyber-attack could inflict on your business.
Unauthenticated Testing
Unauthenticated web app testing replicates the actions of a cybercriminal who operates from a publicly available webpage, without possessing valid user credentials. By conducting unauthenticated tests, we uncover vulnerabilities that anyone with access to your web application could exploit.
API Testing
API penetration testing is essential for businesses relying on web-based APIs. By combining web app and API tests, a comprehensive security evaluation of the digital ecosystem is achieved, identifying potential vulnerabilities, and ensuring robust protection against cyber threats.
Why Choose Praetorian Secure for Your Web App Penetration Testing?
- Unrivaled Expertise
Our team of penetration testers possesses a wealth of knowledge in diverse web application technologies. Their expertise, combined with industry-standard methodologies and toolsets, ensures the most robust assessment of your web apps’ security.
- Trusted Certifications
At Praetorian Secure, our web app pen testers hold independent certifications from esteemed organizations like CISSP, CompTIA Security +, CDPI, MCP and more. These certifications testify to their proficiency and adherence to international standards in the field of penetration testing.
- Trusted by Businesses Worldwide
From global enterprises to SMBs and startups, businesses worldwide trust Praetorian Secure to safeguard their digital assets. Our track record of providing exceptional cybersecurity solutions has earned us the confidence of organizations across the globe.
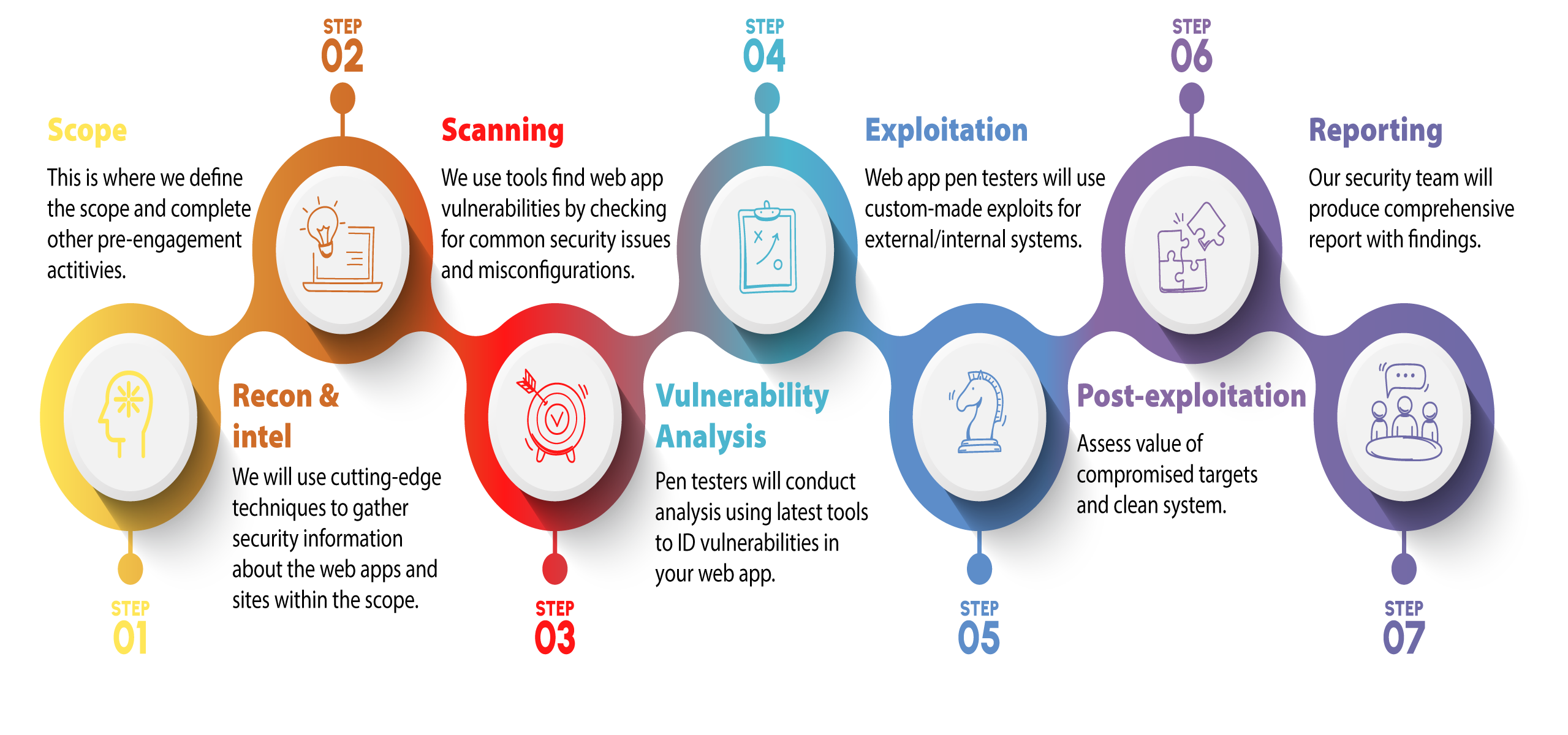
Our Web App Testing Process
The our web app pen test process consists of the following 7 steps:
- Scope Definition & Pre-Engagement Interactions: In this initial phase, the testing scope is defined, and pre-engagement interactions take place to understand the goals and objectives of the penetration test. This includes discussions with stakeholders and defining the boundaries of the test.
- Intelligence Gathering & Threat Modelling: During this phase, comprehensive intelligence is gathered about the target web application and its infrastructure. Threat modeling is also performed to identify potential attack vectors and prioritize testing efforts.
- Scanning: Automated tools are used to scan the web application for common security issues and vulnerabilities. This step provides an initial assessment of the application’s security posture.
- Vulnerability Analysis: Penetration testers conduct a detailed analysis of the web application, manually identifying and verifying vulnerabilities discovered during the scanning phase. This step involves a deeper examination of potential security weaknesses.
- Exploitation: Once vulnerabilities are confirmed, penetration testers attempt to exploit them to gain unauthorized access or control over the web application. This step helps assess the impact and severity of the identified vulnerabilities.
- Post-Exploitation: After successful exploitation, testers may attempt to further pivot through the network and systems to explore potential lateral movement possibilities. This step evaluates the extent to which an attacker can gain access to sensitive data or other critical systems.
- Reporting: A comprehensive report is generated detailing all findings, including identified vulnerabilities, the level of risk they pose, and recommended remediation steps. This report is presented to the stakeholders for review and discussion to help improve the web application’s security posture.
Our Penetration Testing Methodology Vs. Process
A web app pen test process outlines the steps involved in a penetration test, while a methodology offers a more structured and specific approach with detailed guidelines for each testing phase. Our web app security testing process is defined above. Our web app pen testing methodology covers:
- Scope Definition
- Information Gathering
- Threat Modeling
- Vulnerability Scanning
- Manual Testing
- Authentication & Authorization
- Input Validation
- Business Logic Testing
- Session Management
- Error Handling
- API Testing
- Client-Side Testing
- Cryptography
- Reporting
- Remediation Verification
What is the OWASP Top 10?
Web applications are essential for various online activities. However, security risks have also increased. To tackle these challenges, the OWASP Top Ten provides a definitive list of critical web application security risks. Let’s explore this valuable resource and understand its significance in promoting secure web application development.
Why Should You Embrace the OWASP Top 10?
- Proven Effectiveness: An astounding 94% of applications were thoroughly tested for broken access control, a prominent risk identified in the OWASP Top 10. This underlines its undeniable effectiveness in safeguarding against one of the most prevalent security concerns.
- Cryptography Focus: With an increasing emphasis on cryptographic failures, the OWASP Top 10 encourages robust encryption practices to prevent sensitive data exposure and potential system compromises.
- Design Flaw Awareness: A fresh category in the OWASP Top 10 tackles insecure design, encouraging developers to engage in threat modeling and adopt secure design patterns for enhanced resilience against potential vulnerabilities.
- Minimize Misconfigurations: Approximately 90% of applications were meticulously tested for misconfigurations, which can be effectively mitigated by adhering to the guidelines outlined in the OWASP Top 10.
OWASP Top 10 Standard for Web Apps
At Praetorian Secure, we understand the paramount importance of securing your web applications against potential threats, which is why our comprehensive and professional approach is anchored in the acclaimed OWASP Top 10. The OWASP Top 10 Web Application Security Risks for 2021 are as follows:
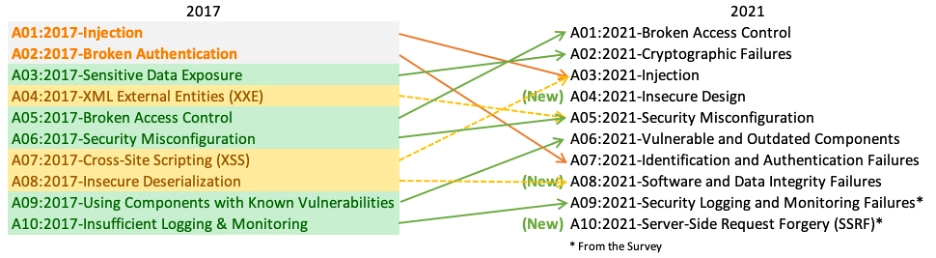
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures (previously Sensitive Data Exposure)
- A03:2021-Injection (includes Cross-site Scripting)
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration (includes former XML External Entities category)
- A06:2021-Vulnerable and Outdated Components (previously Using Components with Known Vulnerabilities)
- A07:2021-Identification and Authentication Failures (previously Broken Authentication)
- A08:2021-Software and Data Integrity Failures (includes former Insecure Deserialization category)
- A09:2021-Security Logging and Monitoring Failures (previously Insufficient Logging & Monitoring)
- A10:2021-Server-Side Request Forgery
OWASP Top 10 Mapping from 2017 to 2021
Frequently Asked Questions About Web App Security Testing
Web Application Security is the process of identifying vulnerabilities in web applications to mitigate potential security risks. It works by using a combination of manual and automated testing techniques to identify potential security risks.
Web app security testing is important because it helps identify vulnerabilities in web applications that can be exploited by cybercriminals. By identifying and mitigating these risks, organizations can protect their sensitive data and prevent potential financial losses.
The types of web application testing include functional testing, security testing, performance testing, usability testing, and compatibility testing.
Web app security testing is important because it helps identify vulnerabilities in web applications that can be exploited by cybercriminals. By identifying and mitigating these risks, organizations can protect their sensitive data and prevent potential financial losses.
Web app security testing should be performed regularly, ideally after any major changes to the web application. This ensures that any new vulnerabilities are identified and mitigated before they can be exploited by cybercriminals.
The four layers of web application security include the network layer, the server layer, the application layer, and the data layer.
To secure web applications from vulnerabilities in 2023, organizations should implement a comprehensive security testing program, use secure coding practices, implement access controls, use encryption, and keep software up to date.
The attributes of security testing include confidentiality, integrity, availability, and non-repudiation.
Mobile app testing involves testing mobile applications on mobile devices, while web app testing involves testing web applications on web browsers.
API Penetration Testing involves testing the security of APIs, while Web Application Penetration Testing involves testing the security of web applications.
The cost of a web application penetration test varies based on factors such as the application’s size (number of APIs), complexity, testing depth (duration), approach, and number of resources. To request a pen test quotation, kindly reach out to our team and we will set up a meeting to discuss your project in more detail.
Your Web App May Be Vulnerable, Learn How We Can Make It Impenetrable.
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Secure your web applications and APIs with our top-tier web app testing services. Praetorian Secure offers competitive pricing that caters to businesses of all sizes, granting them complete control over their security vulnerabilities. Don’t wait for a cyber-attack to compromise your business; take proactive measures today. Get in touch with us to receive a web app testing quote. Simply fill out the form below: