Building an End-To-End DevSecOps Pipeline: AWS (Amazon Web Services)
Welcome back for part 3 of the DevSecOps Series. In this article we will cover exclusively AWS (Amazon Web Services) tools and services. Furthermore, the example pipeline will utilize some third-party open-source tools for SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), and SCA (Software Composite Analysis). However, they are fully integrated and are critical components of the DevSecOps pipeline in AWS.
DevOps is short for Development (Dev) plus Operations (Ops). Then someone got creative and threw the word Security (Sec) in between to create the latest cybersecurity buzz word, DevSecOps. DevOps is a combination of, “cultural philosophies, practices, and tools that combine software development with information technology operations” (AWS). In other words, the Dev- represents the people and process and Ops- stands for the high-speed processes and teams that monitor and deliver the software. Sec- is the teams and tools that allow for security to be integrated into the build pipeline consistently via automation. DevOps without the integrated security would be considered sub-optimal in a high-maturity application development program.
The purpose of this article is to inform our peers about general tools, services, architecture, and methods used to create a DevSecOps pipeline in Amazon Web Services. Additionally, this post addresses concepts of embedded security within the DevOps pipeline. This will allow business professionals to make better informed decision when considering DevSecOps pipelines and overall program structure. Likewise, this material can help companies improve quality, speed, and innovation while decreasing costs and shrinking development cycles consistently. Meanwhile, maintaining high emphasis on security aspects including continuous testing, security operations, logging and monitoring, and auditing and governance.
According to AWS State of DevOps 2019, “elite DevOps performers had 7x lower change failure rate than lower performers”. Meaning, the more “DevOps” aware a team is the less issues they will have when implementing new code changes. This is just another benefit of using an AWS DevOps pipeline. Below are a few more things to consider when choosing your tooling and build environment this can change based on a case-by-case basis. Consider what is right for your organization or consult with an expert to get help weighing your options.
Adopting AWS For Your DevOps Pipeline Foundation
Organizations create many kinds of software for a multitude of reasons. These range from web apps to standalone apps and so on… the point being with the current demand for high-speed development operations companies have turned to automated and continuous development operations in the cloud. Cloud architecture is more agile and scalable when it comes to DevOps than the traditional monolithic approach. It also allows companies to become more fluid while trying to keep up with ever-changing business needs. Having a well-rounded DevSecOps pipeline plays a major role in creating a successful software development operation that is accepted and scalable organization wide.
Identifying vulnerabilities during the beginning stage(s) of the SDLC (software development life cycle) can significantly reduce the overall cost of developing apps but being able to automate it can accelerate the delivery of these changes up to 106 times faster *lead time from commit to deploy stage (AWS DevOps Report). Integrating tools and aggregate vulnerability findings can be a burden to do from scratch but AWS has the services and tools necessary to accelerate this process and provides the flexibility to build DevSecOps pipelines with straightforward integrations of AWS cloud native and third-party tools.
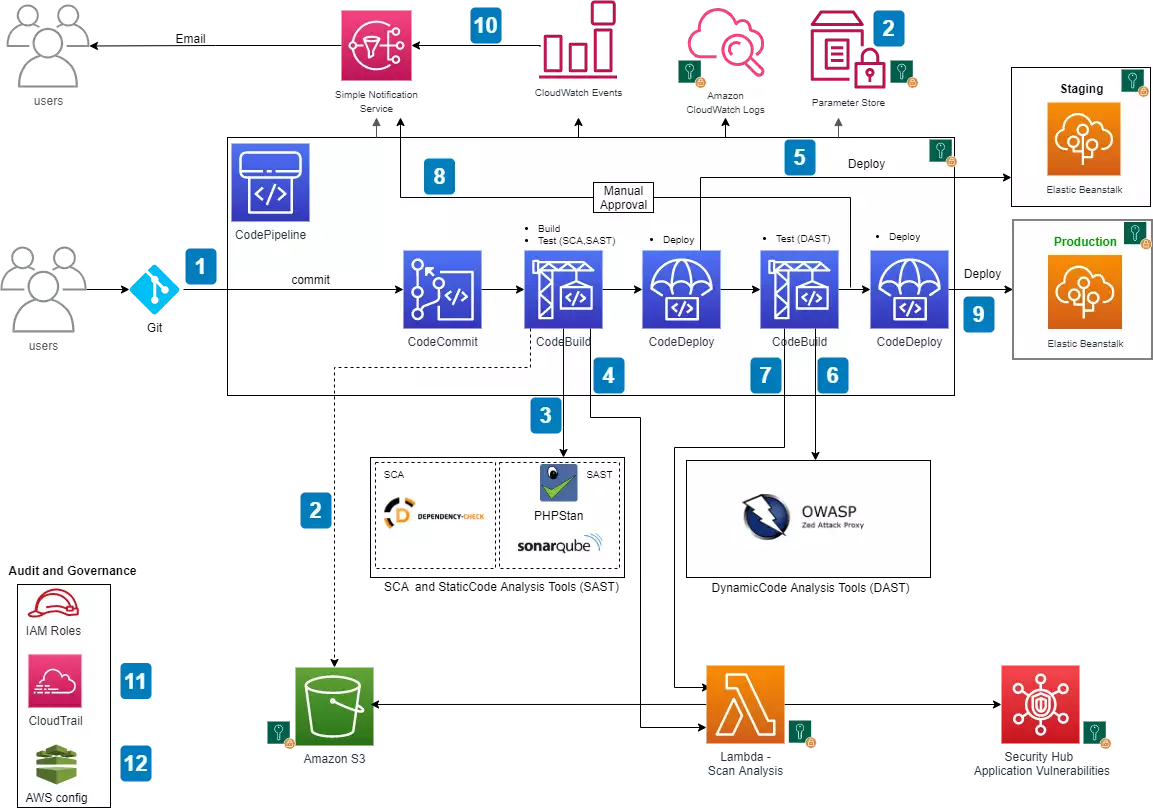
AWS CI/CD Pipeline Architecture – Image Source AWS documentation
Pros of AWS DevSecOps Pipelines
The “benefits” of AWS according to Amazon and online customer reviews include:
- Faster Speeds (all around)
- Rapid Delivery
- High Reliability
- Endless Scalability
- Improved Collaboration
- Increased Security
- Pay as you go (affordable = scalable)
Cons of AWS DevSecOps pipelines
These include the “cons” of AWS from online users. The most notable are as follows:
- Rendering of the page consumes a lot of data and it refreshes continuously
- Integration with build and version control services that are not native to AWS
- Steep learning curve
- Other performance issues
- Not as robust as Azure DevOps
Common Challenges
- Current lack of understanding of DevSecOps and related concepts.
- Finding an advocate/spokesperson and gaining company wide acceptance of the plan.
- Choosing between the trade-offs of different tools and compatibility, integration, etc.
- Determining what tools and architecture makes the most sense for the company’s future and objectives.
- Maintaining compliance with industry regulations.
Best Practices for DevSecOps Using AWS
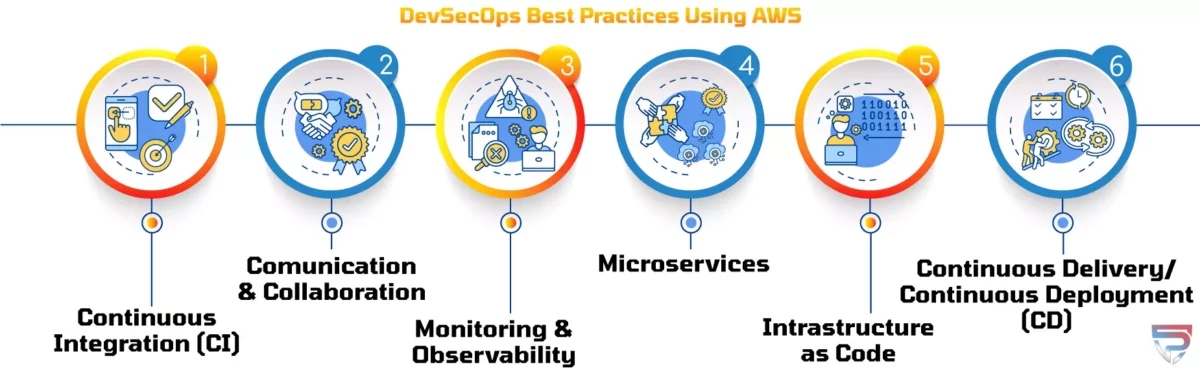
I have left my personal input out to remain un-bias, but TrustRadius gave AWS Codepipeline a score of 8.1 out of 10.
Services and tools Used in The AWS DevOps Pipeline
This section covers various AWS services and third-party compatible tools you can use when building out your DevOps pipeline. Ranging from CI to CD, security and automation, continuous testing, operational services, and more.
CI/CD Services
The following is a list of CI/CD AWS services that lead to innovation for developers.
- AWS CodeBuild – A fully managed continuous integration service that compiles source code, runs tests, and produces software packages that are ready to deploy.
- AWS CodeCommit – A fully managed source control service that hosts secure Git-based repositories.
- AWS CodeDeploy – A fully managed deployment service that automates software deployments to a variety of compute services such as Amazon Elastic Compute Cloud (Amazon EC2), AWS Fargate, AWS Lambda, and your on-premises servers.
- AWS CodePipeline – A fully managed continuous delivery service that helps you automate your release pipelines for fast and reliable application and infrastructure updates.
- AWS Lambda – A service that lets you run code without provisioning or managing servers. You pay only for the compute time you consume.
- Amazon Simple Notification Service – Amazon SNS is a fully managed messaging service for both application-to-application (A2A) and application-to-person (A2P) communication.
- Amazon Simple Storage Service – Amazon S3 is storage for the internet. You can use Amazon S3 to store and retrieve any amount of data at any time, from anywhere on the web.
- AWS Systems Manager Parameter Store – Parameter Store gives you visibility and control of your infrastructure on AWS.
Security & Automation Services
The following are AWS services for continuous logging and monitoring.
- AWS CloudWatch Logs– Allows you to monitor, store, and access your log files from EC2 instances, AWS CloudTrail, Amazon Route 53, and other sources
- AWS CloudWatch Events– Delivers a near-real-time stream of system events that describe changes in AWS resources
- AWS CloudTrail– Enables governance, compliance, operational auditing, and risk auditing of your AWS account.
- AWS Identity and Access Management– Enables you to manage access to AWS services and resources securely. With IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
- AWS Key Management Services (KMS) – Services for creating and managing the encryption keys necessary for data protection. These services use validated hardware security modules to ensure the security of your keys.
- AWS Config– Allows you to assess, audit, and evaluate the configurations of your AWS resources.
Continuous Testing Tools
The following are open-source scanning tools that integrated with AWS in the DevOps pipeline.
- OWASP Dependency-Check– A Software Composition Analysis (SCA) tool that attempts to detect publicly disclosed vulnerabilities contained within a project’s dependencies.
- SonarQube (SAST)– Catches bugs and vulnerabilities in your app, with thousands of automated Static Code Analysis rules.
- PHPStan (SAST)– Focuses on finding errors in your code without running it. It catches whole classes of bugs even before you write tests for the code.
- OWASP Zap (DAST)– Helps you automatically find security vulnerabilities in your web applications while you’re developing and testing your applications.
Operational Services
The following are AWS operations services.
- AWS Security Hub– Gives you a comprehensive view of your security alerts and security posture across your AWS accounts. This post uses Security Hub to aggregate all the vulnerability findings as a single pane of glass.
- AWS CloudFormation– Gives you an easy way to model a collection of related AWS and third-party resources, provision them quickly and consistently, and manage them throughout their lifecycles, by treating infrastructure as code.
- AWS Systems Manager Parameter Store– Provides secure, hierarchical storage for configuration data management and secrets management. You can store data such as passwords, database strings, Amazon Machine Image (AMI) IDs, and license codes as parameter values.
- AWS Elastic Beanstalk– An easy-to-use service for deploying and scaling web applications and services developed with Java, .NET, PHP, Node.js, Python, Ruby, Go, and Docker on familiar servers such as Apache, Nginx, Passenger, and IIS. This post uses Elastic Beanstalk to deploy LAMP stack with WordPress and Amazon Aurora MySQL. Although we use Elastic Beanstalk for this post, you could configure the pipeline to deploy to various other environments on AWS or elsewhere as needed.
Conclusion
All these AWS services work together to create powerful, functional, and scalable pipelines. Nonetheless, achieving a DevSecOps culture can seem distant at first do not give up hope. Good things are soon to come, sometimes all it takes is the right toolset, team, and vision to get the mission accomplished. If your team needs a little boost, our experts can help guide the way and focus your efforts. With options including security training, program assessment and development, and more.
DevOps without security falls short of the target 100% of the time. DevOps with embedded security is the only way to ensure your organization’s Development program reaches full maturity. Also, it lets you take advantage of the expected rewards. Our DevSecOps team has worked with fortune 500 companies to help develop very sophisticated, scalable DevSecOps programs. We take all the difficulty and what ifs out of the equation for you by adding a third-party expert to give you feedback and guidance.
Development and Test on Amazon Web Services (awsstatic.com)
GitHub – sottlmarek/DevSecOps: Ultimate DevSecOps library (https://github.com/sottlmarek)
Serverless CI/CD for the Enterprise on the AWS Cloud (aws-quickstart.s3.amazonaws.com)
AWS Container DevSecOps Workshop (https://github.com/aws-samples/aws-container-devsecops-workshop)
Additional Services our team of cybersecurity engineers can perform:
- Security Testing
- Penetration Testing Services
- Cloud Security Testing
- Network Security Testing
- Web App Testing
- Static Analysis
- DevSecOps
- Application Security
- Managed Security Testing
About Praetorian Secure
At Praetorian Secure we take a sense of pride in the cybersecurity consulting and compliance services we deliver. The goal is to improve an organizations security posture while building confidence and understanding at the same time. Keeping important assets secure from threats since 2009. Praetorian Secure is a Service-Disabled Veteran-Owned Small Business (SDVOSB). Founded by two former U.S. Army Agents of the Certification Authority. Gaining momentum quickly they expanded their locations, adding a branch in South Florida. That is when we decided we wanted to be involved in helping companies achieve compliance or improve their cyber security in a more simplistic, hassle-free manner. Our service expertise includes Compliance Services, DevSecOps, Vulnerability Management, Cloud Security, vCISO, and more.
We have worked with companies across the globe, within varying industries to create a better/stronger/healthier security landscape. Including clients such as MetLife, Xerox, United Health, U.S. Army, Airforce, Navy, and more. We live in a world where threats never stop evolving and hackers do not take any days off – as responsible business owners/employees we must not ignore this reality. If you are interested in learning more, please contact us via phone at +1 (855) 519-7328 or at info@praetoriansecure.com.
Securing today, for a safer tomorrow!
Works Cited
“Accelerate State of DevOps 2019.” Google Cloud, 2019, services.google.com/fh/files/misc/state-of-devops-2019.pdf.
Manepalli, Srinivas. “Building an End-to-End Kubernetes-Based DevSecOps Software Factory on AWS.” Amazon Web Services, AWS, 26 June 2021, aws.amazon.com/blogs/devops/building-an-end-to-end-kubernetes-based-devsecops-software-factory-on-aws.
—. “Building End-to-End AWS DevSecOps CI/CD Pipeline with Open Source SCA, SAST and DAST Tools.” Amazon Web Services, AWS, 22 Jan. 2021, aws.amazon.com/blogs/devops/building-end-to-end-aws-devsecops-ci-cd-pipeline-with-open-source-sca-sast-and-dast-tools.



